Flaws in Netgear Routers Expose Users to Surveillance, Malware, and Remote Attacks
Up to five security vulnerabilities have been revealed in Netgear RAX30 routers, which could be linked together to circumvent authentication and enable remote code execution.
“Successful exploits could allow attackers to monitor users’ internet activity, hijack internet connections, and redirect traffic to malicious websites or inject malware into network traffic,” a report from Claroty security researcher Uri Katz noted.
Moreover, the vulnerabilities could be exploited by a malicious actor situated near the network to take advantage of the weaknesses and gain unauthorized access to networked intelligent gadgets such as security cameras, thermostats, and smart locks. The attacker could also manipulate router configurations and leverage the compromised network to launch assaults on other networks or devices.
The following is a list of flaws that were exhibited during the Pwn2Own hacking competition that took place in Toronto in December 2022:
- CVE-2023-27370 (CVSS score: 5.7) – Device Configuration Cleartext Storage Information Disclosure Vulnerability
- CVE-2023-27369 (CVSS score: 8.8) – Stack-based Buffer Overflow Authentication Bypass Vulnerability
- CVE-2023-27367 (CVSS score: 8.0) – Command Injection Remote Code Execution Vulnerability
- CVE-2023-27357 (CVSS score: 6.5) – Missing Authentication Information Disclosure Vulnerability
- CVE-2023-27368 (CVSS score: 8.8) – Stack-based Buffer Overflow Authentication Bypass Vulnerability
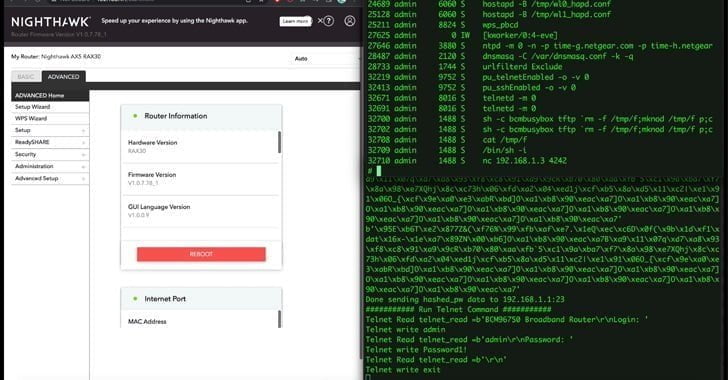
The industrial cybersecurity company demonstrated a proof-of-concept exploit chain that reveals how vulnerabilities (CVE-2023-27357, CVE-2023-27369, CVE-2023-27368, CVE-2023-27370, and CVE-2023-27367) can be linked together in sequence to extract the device’s serial number and gain root access.

“These five CVEs can be chained together to compromise affected RAX30 routers, the most severe of which enable pre-authentication remote code execution on the device,” Uri Katz wrote.
Netgear has recommended that individuals using RAX30 routers update to firmware version 1.0.10.94, which was released by the networking company on April 7, 2023, in order to tackle any issues and reduce the likelihood of potential hazards.