More than a Dozen Chrome Extensions Caught Hijacking Google Search Results for Millions of Users
(The AEGIS Alliance) – New details have emerged about a huge network of rogue browser extensions for Chrome and Edge that have been discovered to hijack clicks to hyperlinks in search results pages to arbitrary URLs that include phishing websites and advertisements.
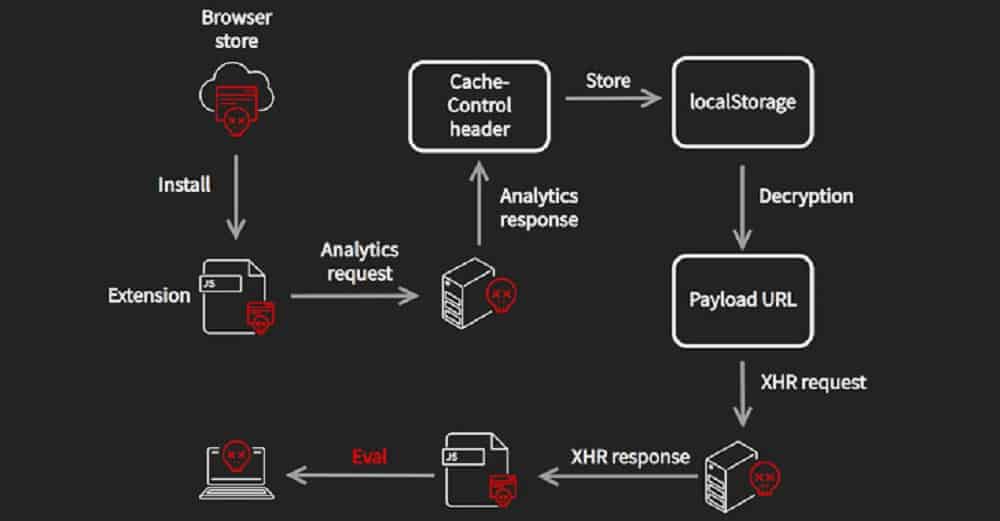
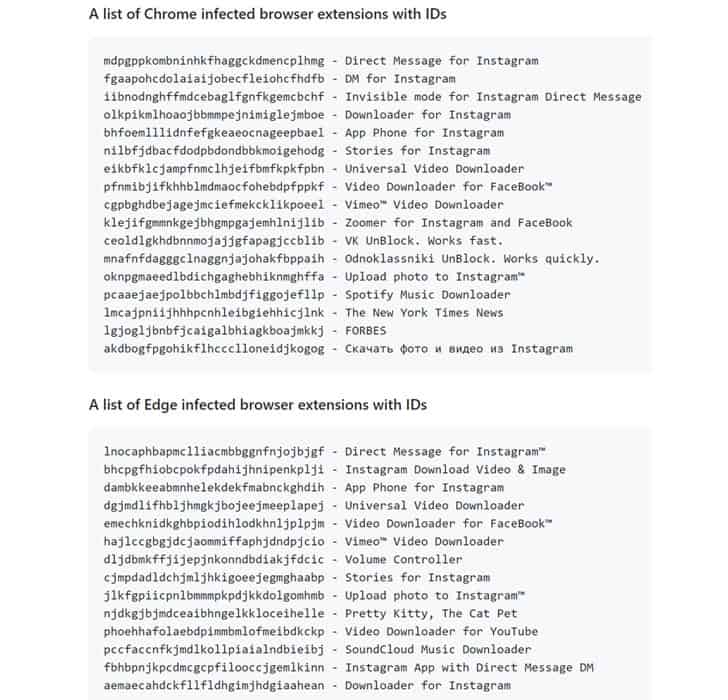
Collectively referred to as “CacheFlow” by Avast, the 28 extensions in question include Instagram Story Downloader, Video Downloader for Facebook, Vimeo Video Downloader, and VK Unblock. They’ve made use of a sneaky trick that masks its true function: Leverage Cache-Control HTTP header as a covert channel to get commands from a server controlled by an attacker.
All the backdoored browser extensions were removed by Google and Microsoft as of December 18, 2020, to prevent additional users from downloading them from the official stores.
According to telemetry information gathered by the firm, the highest three contaminated countries had been Brazil, Ukraine, and France, followed by Argentina, Spain, Russia, and the United States.
The CacheFlow sequence started when unsuspecting users downloaded one of the extensions for their browsers that, upon being installed, sent out analytics requests resembling Google Analytics to a remote server, which then beamed a specially-crafted Cache-Control header back that contained hidden instructions to fetch a second-stage payload that functioned as a downloader for the final JavaScript payload.
This JavaScript malware gathered a massive amount of birth dates, electronic mail addresses, geolocation data, and device activity, with a particular concentration on amassing the information from Google.
“To retrieve the birthday, CacheFlow made an XHR request to https://myaccount.google.com/birthday and parsed out the birth date from the response,” Avast researchers Jan Vojtěšek and Jan Rubín noticed.
In the final step, the payload injected one other piece of JavaScript into every tab, utilizing it to hijack clicks that lead to reputable sites, and it additionally modified search results from Google, Bing, and Yahoo to reroute the victim to a different URL.
That’s not all. The extensions didn’t solely prevent infecting users who had been more likely to be web developers, one thing that was deduced by computing a weighted rating of the extensions installed or by checking in the event that they accessed locally-hosted websites (e.g., .dev, .local, or .localhost), they have also been configured to not exhibit any suspicious behavior in the course of the first three days after installation.
Avast mentioned the myriad tricks employed by the malware authors to avoid being detected could have been an important factor that allowed it to execute malicious code in the background and stealthily infect victims in the millions, with evidence that suggests the campaign could have been active since at least October 2017.
“We usually trust that the extensions installed from official browser stores are safe,” the researchers stated. “But that is not always the case as we recently found.”
“CacheFlow was notable in particular for the way that the malicious extensions would try to hide their command and control traffic in a covert channel using the Cache-Control HTTP header of their analytics requests. We believe this is a new technique.”
The full list of indicators of compromise (IoCs) related to the campaign may be accessed right here.
Kyle James Lee – The AEGIS Alliance – This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.